The new design resulted in a 25% reduction in investigation time and a 20% increase in threat detection accuracy, enabling security teams to respond faster and more effectively. Key KPIs included a significant improvement in time to resolution and threat detection accuracy, alongside higher user satisfaction scores from analysts, who reported smoother workflows and quicker access to critical data. The platform saw a strong adoption rate within the first quarter, with analysts utilizing key features to enhance their response rates to high-priority alerts, ultimately driving better security outcomes.
TruSTAR
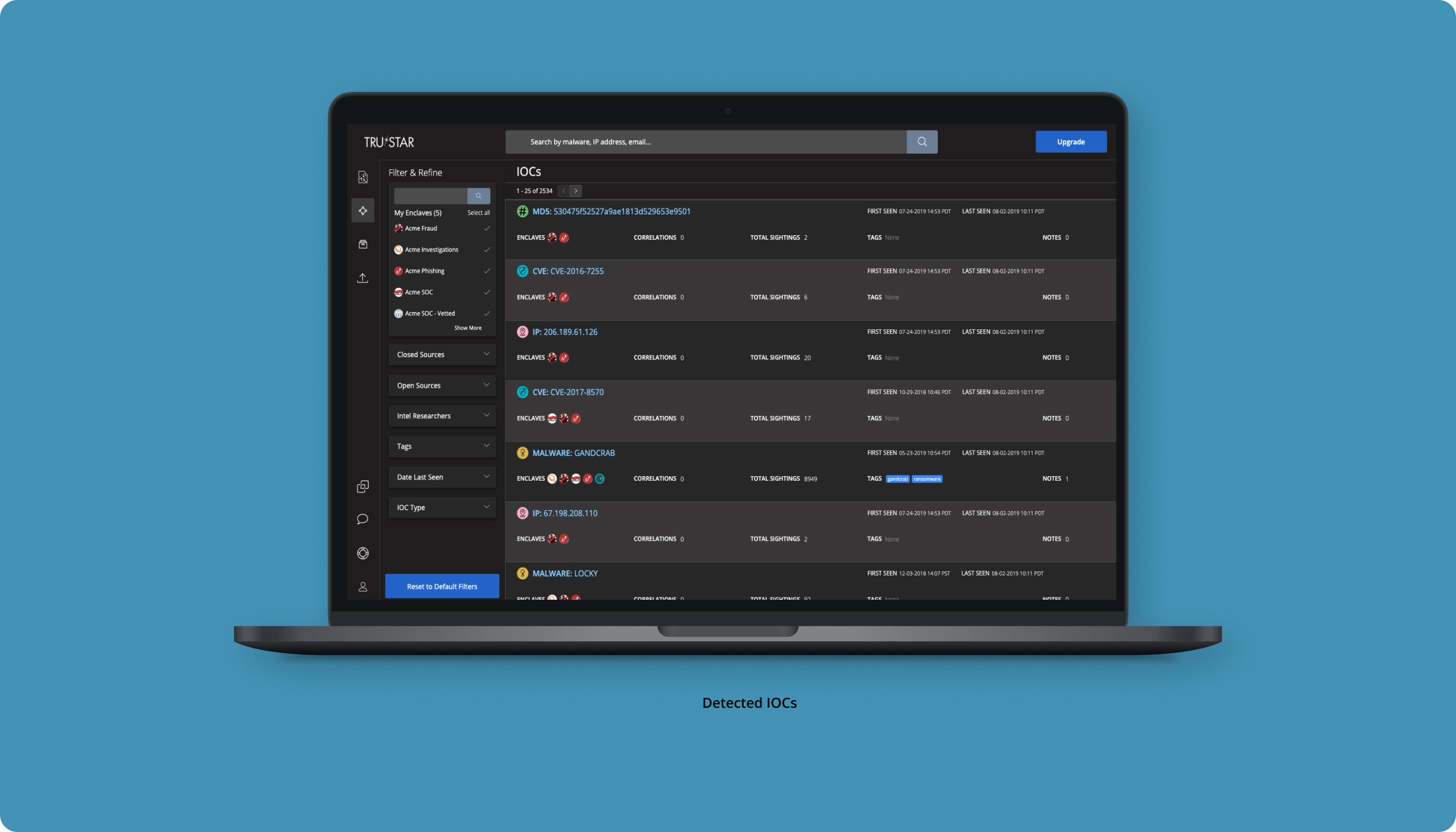
TruSTAR is a cybersecurity company that provides intelligence management tools to help organizations centralize, normalize, and automate the handling of threat intelligence data. Their platform enables security teams to correlate internal incident data with external threat intelligence sources to improve the speed and accuracy of threat detection, investigation, and response.
Task
Sharing and Collaboration: Allowing organizations to securely share threat data within their teams and with trusted partners.
The goal of this project was to enhance TruSTAR’s intelligence management platform, enabling security teams to efficiently centralize, normalize, and automate the handling of threat intelligence data. The focus was on improving the correlation of internal incident data with external threat sources, optimizing the platform’s user experience to boost the speed and accuracy of threat detection, investigation, and response. By streamlining workflows and providing actionable insights, the redesigned platform aimed to empower security teams with faster, more precise decision-making capabilities.
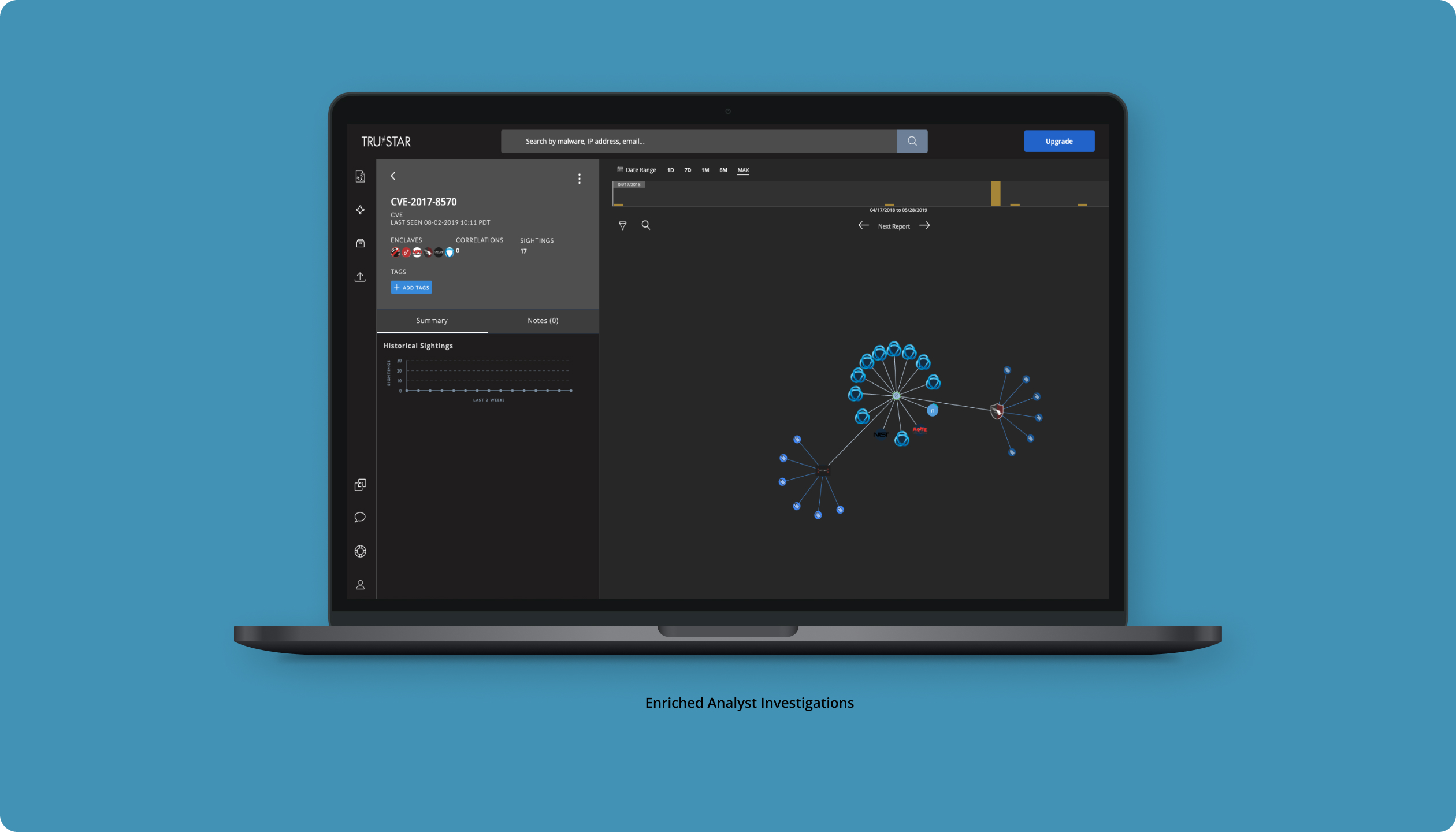
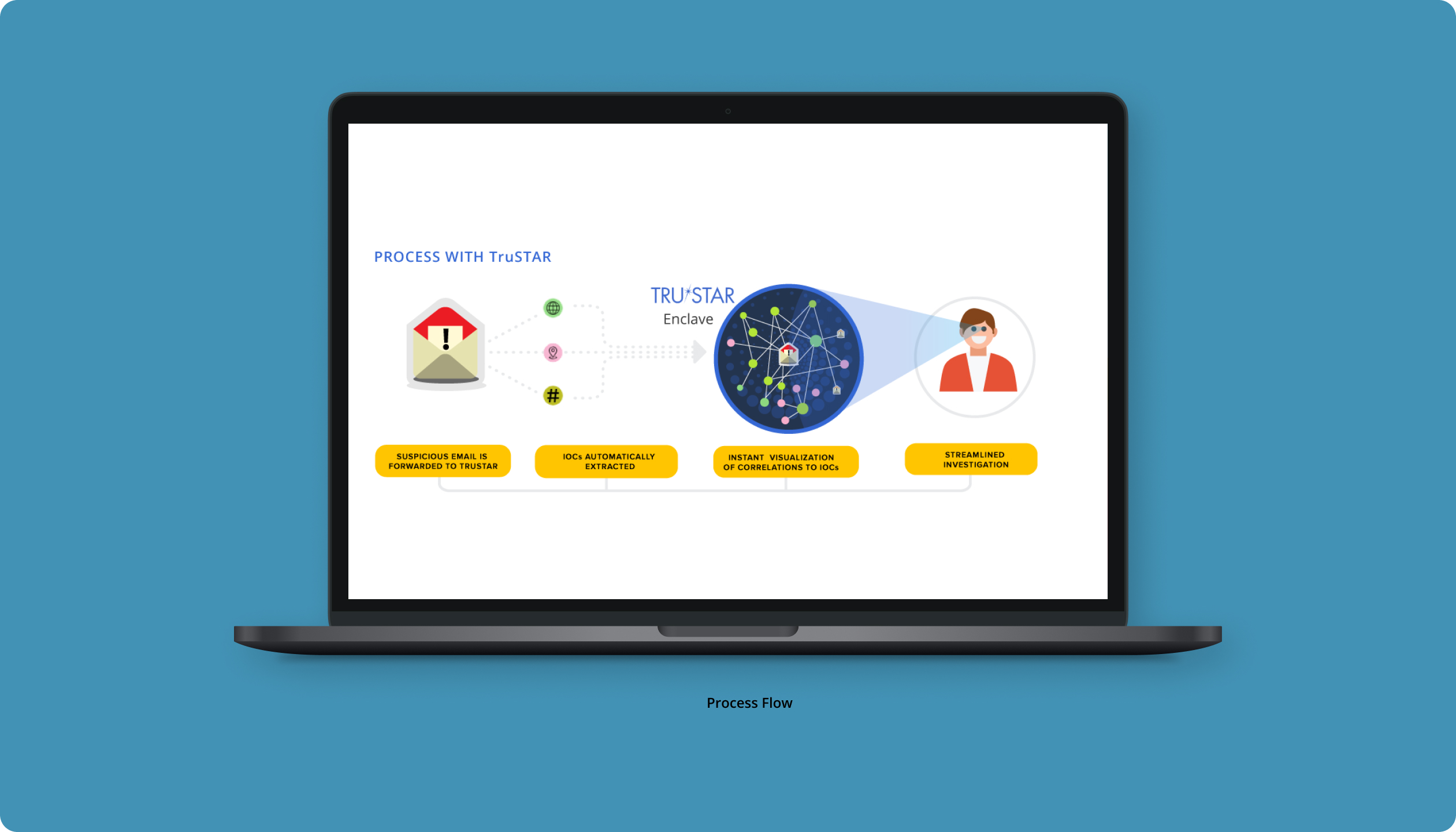
When designing for TruSTAR’s threat intelligence platform, my approach centered on understanding the unique workflows of security analysts and the challenges they face in correlating large volumes of threat data. By focusing on automating data aggregation and prioritizing actionable insights, I ensured the interface was intuitive and streamlined. This approach also considered the need for customization across different sectors, enabling seamless integration of internal and external intelligence sources to improve threat detection and response times.
Design an intuitive, real-time interface that streamlines threat intelligence management for security teams, enabling seamless data correlation and analysis through automated workflows and customizable integrations.