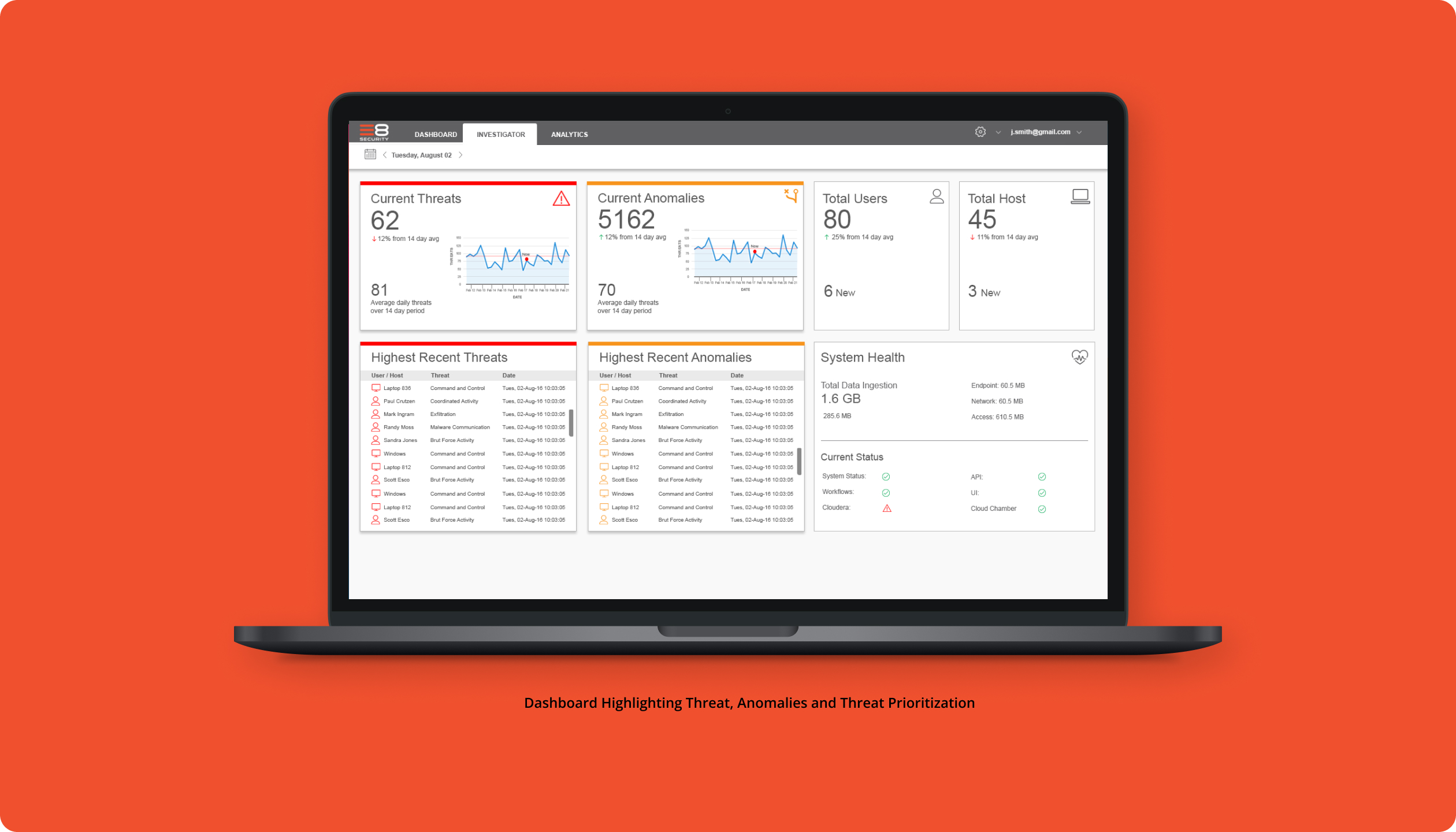
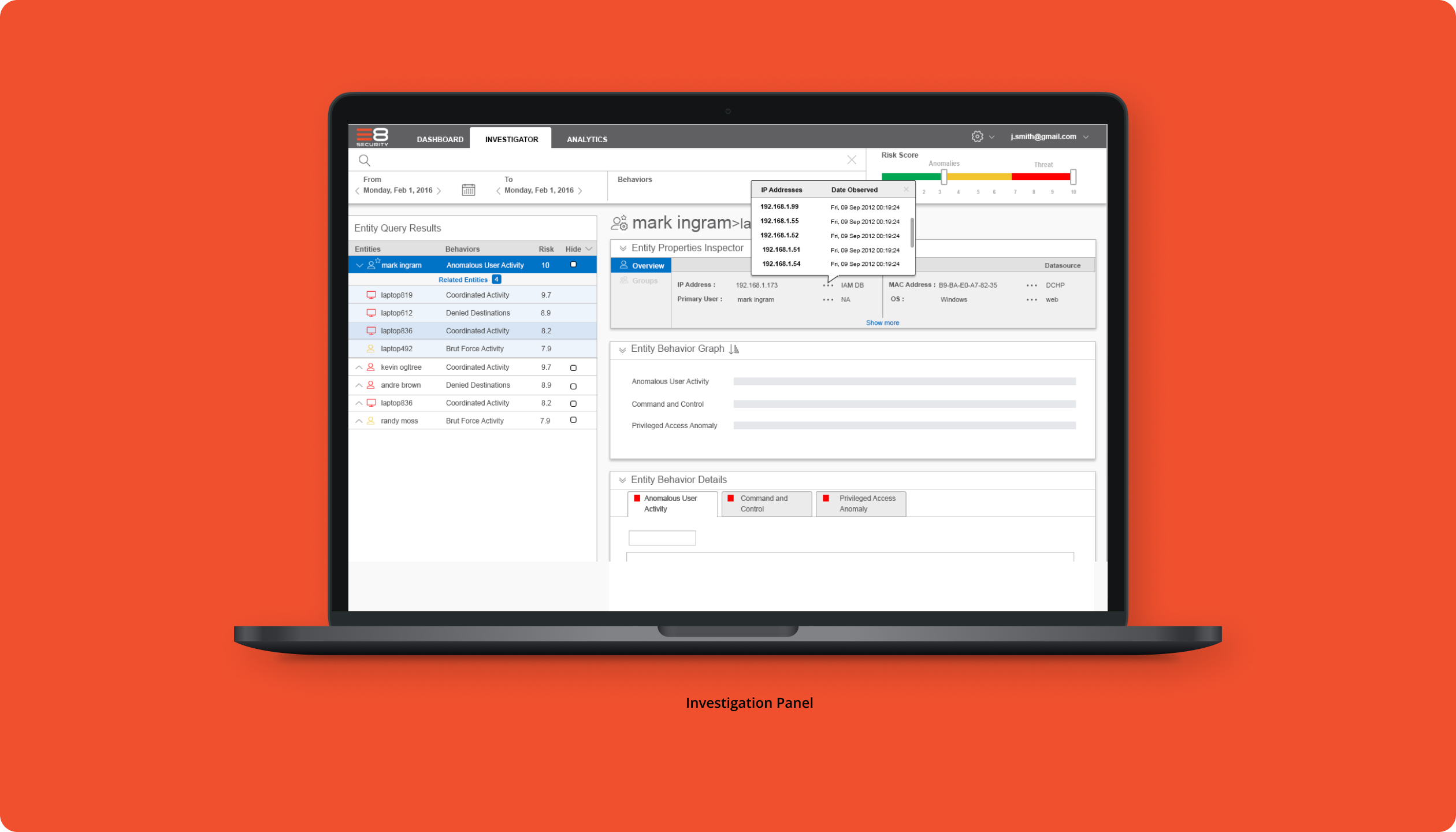
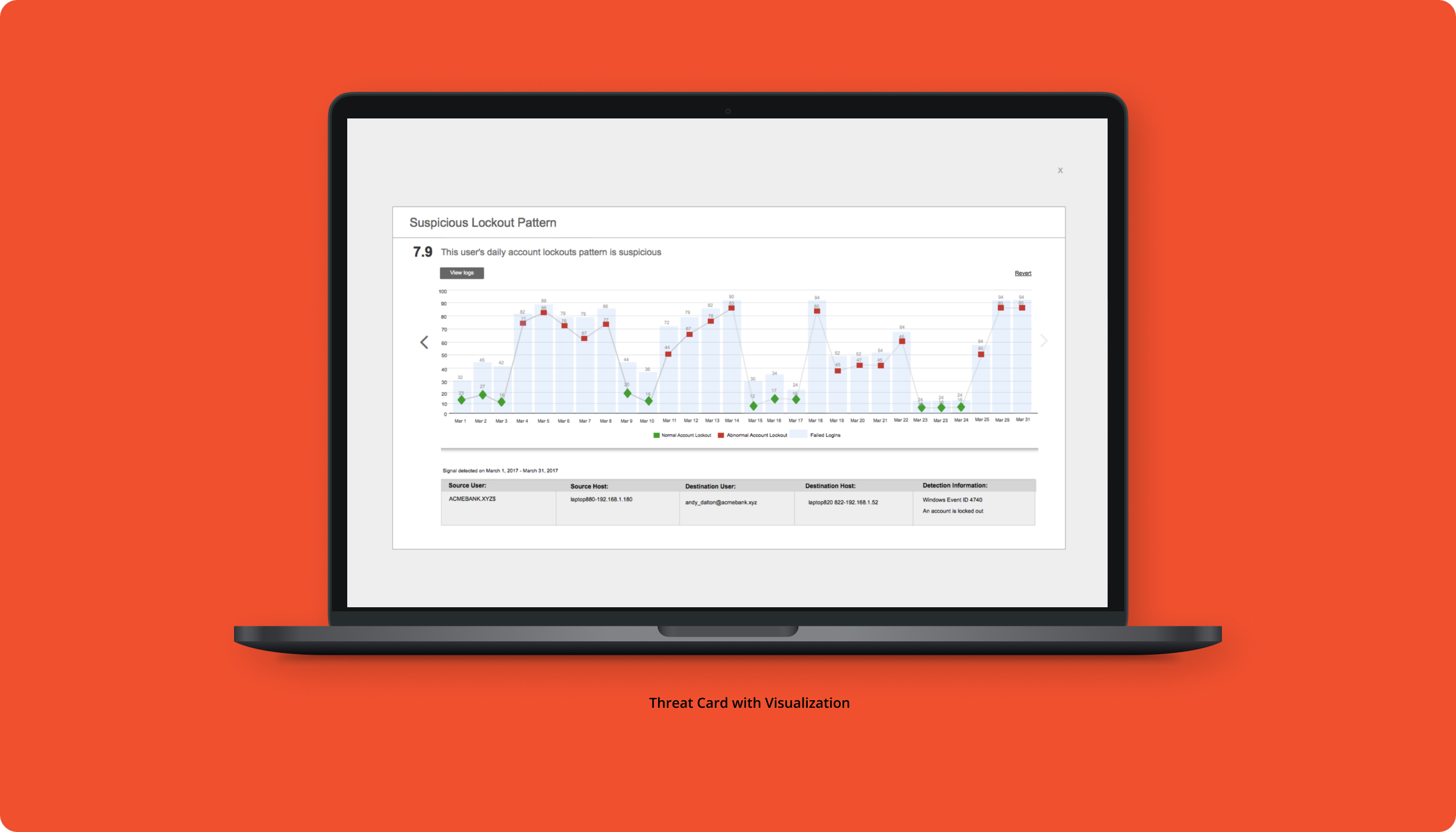
Increased analyst efficiency in identifying and responding to security threats, leading to a 30% reduction in investigation time and improved detection accuracy.
E8 Security
E8 Security was a cybersecurity company that specialized in behavioral analytics and anomaly detection for enterprise security. Their platform utilized machine learning and advanced analytics to detect insider threats, data breaches, and suspicious activity by analyzing user and entity behavior (UEBA). E8 Security was eventually acquired by VMware in 2018, and its technology was integrated into VMware’s security offerings, particularly in their Workspace ONE Trust Network for enhanced threat detection and response.
Task
Create intuitive and visually compelling dashboards for security analysts to monitor and investigate anomalies using behavioral analytics.
The objective of this project was to enhance the user experience of E8 Security’s behavioral analytics platform, making it the go-to tool for security analysts to detect, investigate, and respond to potential threats. Our goal was to redesign the interface to improve data visualization and streamline workflows, while maintaining alignment with the platform’s existing design principles.
Cybersecurity tools must empower analysts to quickly assess and act on complex threat data, with intuitive dashboards, real-time alerts, and seamless data correlation. With these needs in mind, we incorporated several key enhancements, including a simplified alert system and improved visual tools for threat analysis. These updates not only provide greater efficiency for security teams but also enhance the platform’s overall usability and performance. By focusing on these critical elements, we aimed to make E8 Security’s platform an indispensable tool for protecting organizations from evolving threats.
When designing for E8 Security’s behavioral analytics platform, my approach focused on deeply understanding the workflows of security analysts and how they respond to potential threats. I prioritized designing interfaces that simplified complex data, enabling users to quickly assess and investigate anomalies. By tailoring the user experience to highlight high-risk behaviors and refining the interaction flow for efficient investigation, I ensured that the platform was both intuitive and effective in enhancing security operations.
My research focused on understanding the workflows and pain points of security analysts through user interviews and usability testing. I also conducted field studies to observe real-world threat detection, ensuring the design supported fast and accurate decision-making. This research informed intuitive interfaces that streamlined complex data and enhanced threat investigation efficiency.
Analyzed existing security data to understand common threats, response times, and areas where automation could significantly reduce manual effort. This quantitative data informed the design of both custom and boilerplate security flows.
Analyzed existing security data to understand common threats, response times, and areas where automation could significantly reduce manual effort. This quantitative data informed the design of both custom and boilerplate security flows.
By combining user flows, IA, and fidelity prototyping, I not only crafted a user-friendly design but also created a strong foundation for informed design decisions. This approach helped me validate assumptions, refine the user experience, and ultimately develop a product that resonated with users and met their needs.