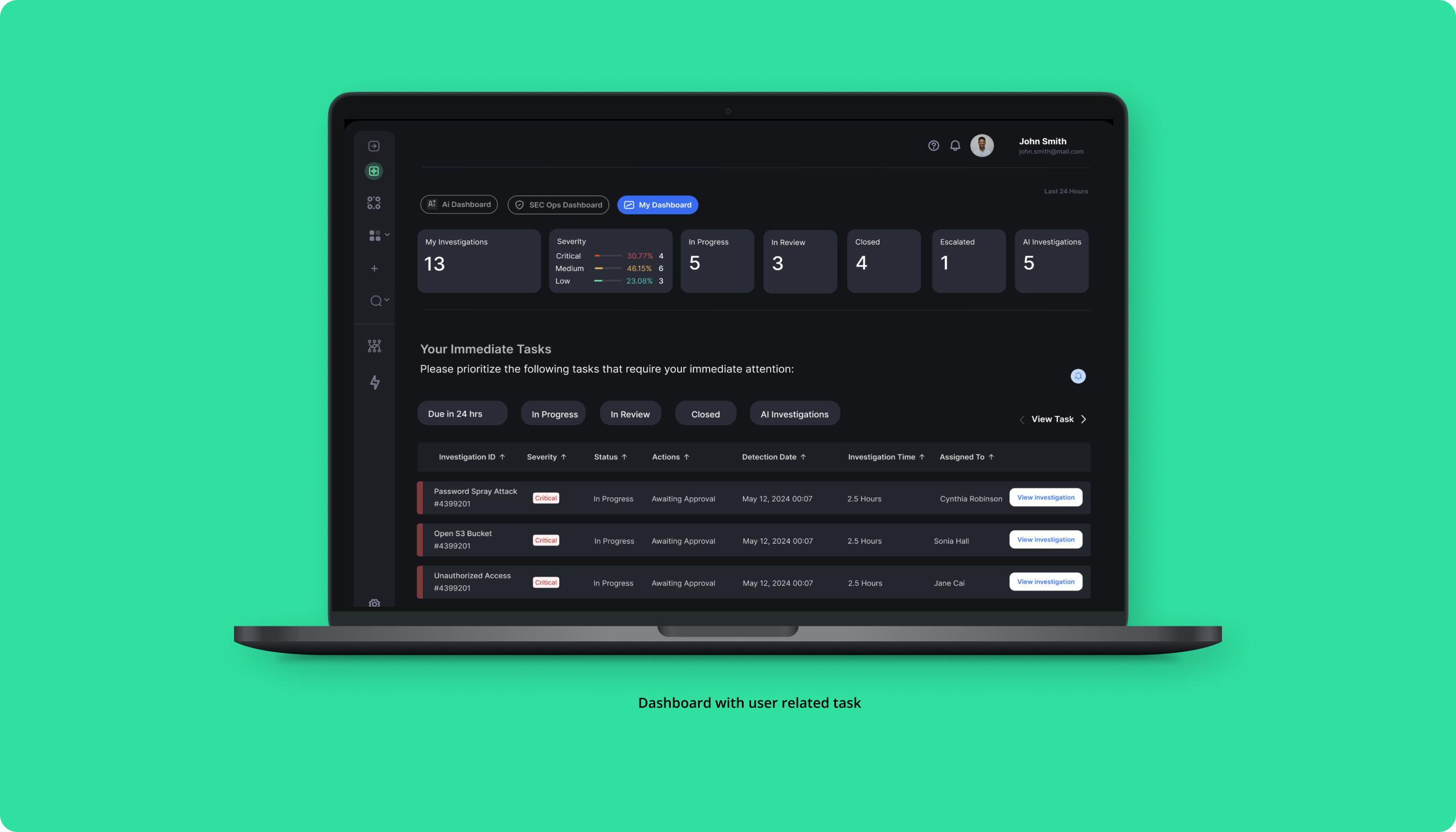
The implementation of these AI-driven security flows will result in a significant reduction in manual workload, improved response times to security incidents, and enhanced overall security posture for the organizations using the product. SOCs will be able to adapt to new threats faster and more effectively, ensuring continuous protection in a dynamic environment.
Stealth Start Up
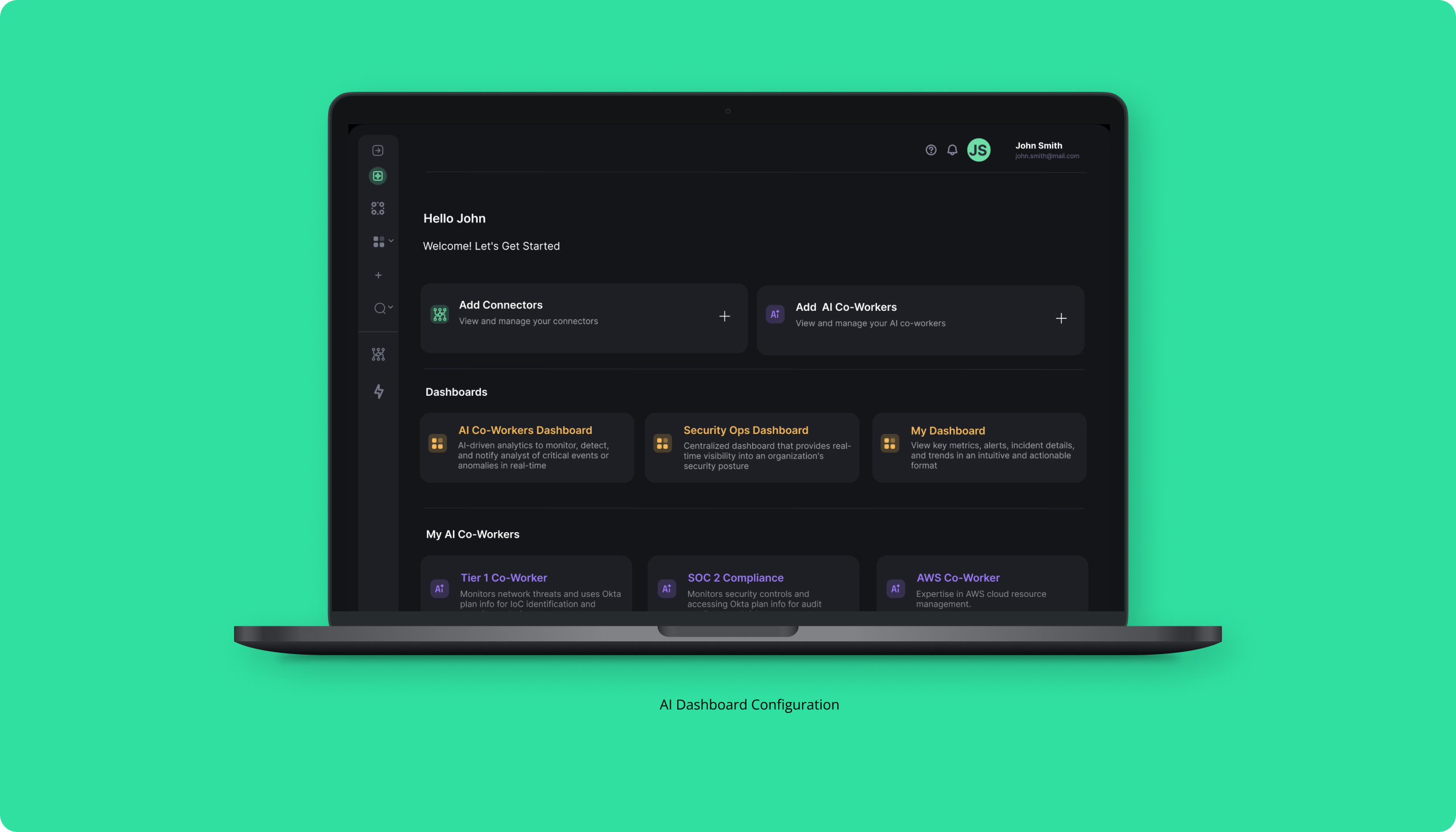
In today’s rapidly evolving digital landscape, businesses face an increasing number of security challenges. To address these challenges, I developed a product that creates custom and boilerplate AI co-worker security flows, designed to streamline and enhance security operations across various industries.
Task
Transforming Security Operations with AI-Driven Workflows
The objective of this project was to develop an intuitive platform for a stealth startup, designed to seamlessly integrate AI co-workers into security teams’ workflows. Our goal was to create a digital experience that enhances collaboration between human analysts and AI, improving the detection and response to security threats while maintaining the platform’s streamlined and user-friendly interface.
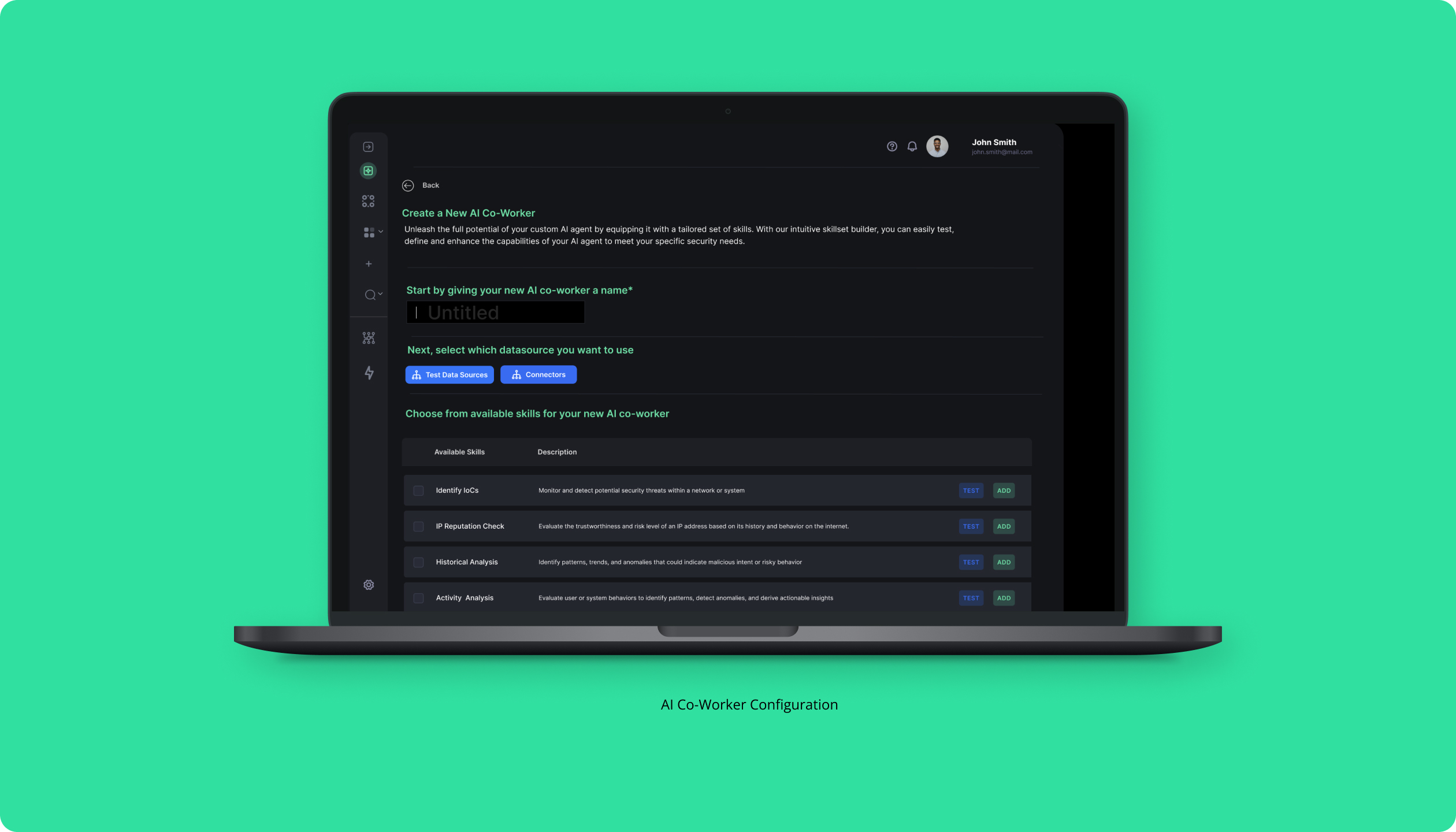
In a security environment, AI co-workers must assist with real-time threat analysis, automate repetitive tasks, and provide actionable insights, all while ensuring trust and transparency. With these requirements in mind, we introduced several key features, such as adaptive AI workflows and customizable interfaces. These updates empower security teams to respond faster and more effectively to emerging threats, making the platform an indispensable tool in the evolving landscape of AI-driven security solutions
I adopted a comprehensive and strategic approach to develop the AI-driven security flows product, combining methods such as user research, data analysis, prototyping, and iterative testing.
Create a dual approach—enable businesses to create both custom AI-driven security workflows tailored to their specific requirements, as well as utilizing boilerplate flows for quicker deployment. This flexibility allows organizations to scale their security operations efficiently, reducing manual intervention and minimizing the risk of human error.